Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 A company calls us in a panic on a Monday morning following a ransomware attack. A disaster scenario that we know well at Present. Cyberattackers often take advantage of the weekend to infiltrate the network of a vulnerable SME by exploiting security flaws. On Monday morning, employees return to their desk, only to find their workstations are crypto-locked, impossible to work or perform tasks as innocuous as sending an email. In addition to the lack of productivity and the reputational damage, important and confidential data is now inaccessible and even worse, sold on the Dark Web. A ransom is now demanded, but paying it is out of the question.
A company calls us in a panic on a Monday morning following a ransomware attack. A disaster scenario that we know well at Present. Cyberattackers often take advantage of the weekend to infiltrate the network of a vulnerable SME by exploiting security flaws. On Monday morning, employees return to their desk, only to find their workstations are crypto-locked, impossible to work or perform tasks as innocuous as sending an email. In addition to the lack of productivity and the reputational damage, important and confidential data is now inaccessible and even worse, sold on the Dark Web. A ransom is now demanded, but paying it is out of the question.
Now the following questions arise:
- What to do?
- How do we prevent this from happening to us (again)?
We explain here how to establish a recovery plan if you have unfortunately been the victim of a ransomware attack, but above all we explain how to prevent such a situation from happening in the first place.
At the end of the blog, we also share with you our 15 cybersecurity essentials.
You have been attacked, what's next?
Realizing that your business is the victim of a ransomware attack is stressful. Nevertheless, the first thing to do is to try to react calmly. These additional policies can help you prevent broader network infiltration and regain access to computers and files.
Communicate with insurers and law firms:
You must first contact your lawyers and your insurer to inform them of the security incident. They will also tell you the specific approach to take depending on your coverage and their incident management policies.
No communication/comment should circulate:
Do not communicate or respond to requests or social media comments from anyone and advise all staff to do the same. Let the specialized services of your lawyers manage the communications.
Disconnect:
Disconnecting the infected device from the Internet and any other device is necessary for the security of the network as a whole. However, you should not shut down or restart your computer.
Several attack methods inject "Services" which are activated in the start-up cycle, often even before the protection tools are activated, which can cause damage and even more rapid propagation.
It is also important to temporarily disconnect all of your shared drives until you have determined that all infected systems have been identified. Continue to monitor systems to identify if there are any new or missing files.
Prepare a network segmentation:
Once the threat has been identified and isolated, in order to be able to perform recovery steps, it is important to define a network segment that is completely isolated from the affected network.
Reimaging your working machines:
Once an environment has been infected, there is no way to guarantee that the ransomware is completely gone unless you wipe the devices, as well as clean VMs, and start with a fresh image. Reimaging servers and applications ensures that the ransomware has been remediated. You can rebuild your network and workstations from scratch by applying cyberattack prevention tools.
Check your backups:
Depending on your disaster recovery plan, you should be able to recover your data from backups. However, you must check them beforehand in case they are invalid or encrypted.
If you have an “Air Gap” type backup, you will most likely be able to recover your information.
Avoid restoring "System" opt more for data recovery only.
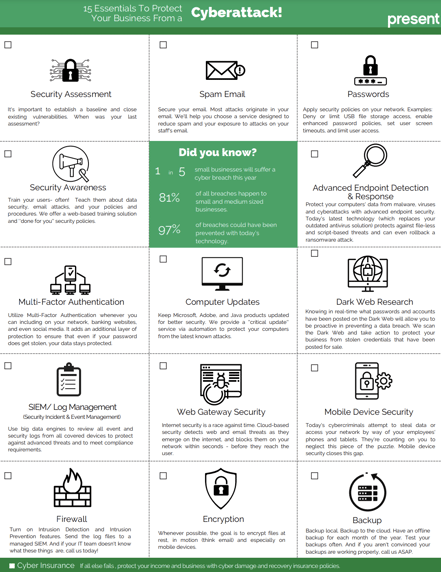
To prevent such an attack, here are our recommendations
Put in place a MDR and a MFA:
90% of threats could be stopped with a MFA installed. One of the most common ways adversaries gain access to corporate data is by guessing weak passwords or stealing them, whether through phishing or buying them from the Dark Web.
From there, they get the same permissions as legitimate users including administrators and power users.
The goal of multi-factor authentication (MDR) is to create an additional layer of defense beyond just using a password by adding a physical factor to it.
Additionally, a MDR service allows you to protect your terminals well beyond what a simple antivirus can do. A managed detection and response solution provides the following benefits:
- Allows the detection of suspicious behaviors used by hackers and malicious software such as the exploitation of vulnerabilities or the elevation of privileges.
- 24/7 monitoring by security analysts.
- During attacks, the attacked terminal is isolated from the network in order to contain the threat.
- Improved threat intelligence based on indicators and behaviors captured from global information.
Set up a backup policy:
A backup policy is a set of rules and procedures that describes a strategy when creating backup copies of data to be retained. A corporate data backup policy is an integral part of an organization's overall data protection, disaster recovery, and business continuity strategy.
Applying the 3-2-1-1-0 rule is the best way to protect your backups. 3 copies of data (one of which is the production data set) must be saved on 2 different types of media where 1 copy must be located offsite and at least 1 of the copies must be stored offline. The 0 refers to the verified integrity of the backup and guarantees that it contains 0 errors.
Establish an incident response plan:
In the event of cyber incidents or data breaches, time is of the essence. The sooner you can contain the damage and identify the cause, the better. This is where an incident response plan comes in. By having a clear, well-documented plan on how to identify and handle an information security incident, you can ensure your team is ready to take quick and effective action.
When designed and implemented correctly, a cybersecurity incident response plan can also provide a structure to prevent future attacks by identifying weaknesses and gathering valuable threat intelligence.
Conclusion
Managing your business' security requires a team of experts who will be able to support you in order to guarantee the security of your corporate data. To find out more about how Present can support you, do not hesitate to contact us!
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)