Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 Regardless of your industry, business size, and IT environment, it is safe to assume that you will experience multiple security incidents that jeopardize the confidentiality, integrity, and availability of your data, and ultimately your business.
Regardless of your industry, business size, and IT environment, it is safe to assume that you will experience multiple security incidents that jeopardize the confidentiality, integrity, and availability of your data, and ultimately your business.
These will range from minor incidents causing limited damage to major incidents with a much greater, even widespread, impact on your organization.
As proof, according to a recent study, more than half of Quebec SMEs have been victims of a cyberattack in the past year.
Cyber incidents are therefore not a mere possibility, but a reality that particularly affects SMBs, because they are easier and more numerous prey than larger companies.
But are you ready to face it?
To understand how prepared you are for an attack, try to answer the following questions:
- What means do you have in place to detect and identify malicious activities in your environment?
- What is your plan to contain threats, once identified?
- How quickly would you be able to recover and get back to normal?
- Would you be able to perform post-incident analysis to improve your security posture?
SMBs cannot prevent all attacks, but they can implement an incident response plan.
We all know the saying prevention is better than cure.
In terms of cyber security, the best attack is the one that fails, because you have been able to identify your flaws and vulnerabilities, and protect yourself against them.
But current events show us that, although necessary, prevention alone is simply not sufficient.
And, to quote Louis Pasteur, "chance favors the prepared mind",
The longer it takes you to detect and respond to a cyber incident, the more you are at risk of suffering severe data loss and significant damage to your bottom line and reputation.
This is why, when cyber incidents occur, it is essential to detect them as early as possible and to react quickly and effectively, in order to mitigate the impacts on your organization, and thus limit your overall costs.
You need a security incident response plan.
It should also be mentioned that this plan is often a requirement of your cyber insurer, but also that it could help with compliance for regulations such as GDPR or Law 25 of Quebec.
How could you report a data breach if you aren't able to even detect it, and how could you respond to it if you don't have a plan?
What is a Security Incident Response Plan?
An incident response plan is a documented set of steps you must follow following a security incident.
Having such a plan in place ensures that your business is prepared for incidents and therefore has the right resources and procedures in place to detect incidents and reduce the recovery time and costs associated with the breach.
Several frameworks have been developed to guide organizations in this planning, including that of the National Institute of Standards and Technology (NIST).
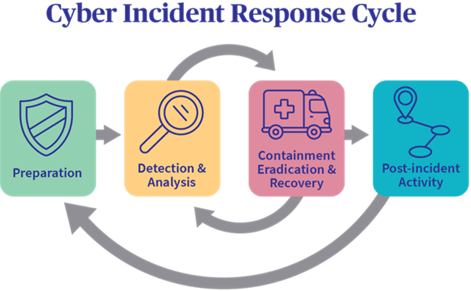
Each phase includes a number of steps that an organization should incorporate into its plan. Let's take a brief look at each of these phases.
Preparation
Your SME must be ready to face a security incident and you must therefore plan all the necessary intervention procedures.
The preparation phase should include planning the actions required to prevent a data breach or attack.
Detection and analysis
The key word is visibility. Your SME must be able to detect incidents and have the tools and technologies to collect, document and analyze data relevant to the incident. Consider, for example, SOC services and EDR and SIEM technologies.
Containment, eradication and recovery
Your SMB must be able to effectively manage an attack, remove the threat from the environment, and restore services.
You also need to gather evidence about the incident.
Post-incident activity
After properly handling a security incident, your SMB should use the lessons learned to improve its incident response plan.
An untested plan is almost equivalent to no plan
As Mike Tyson said, "Everyone has a plan until they get punched in the face."
The effectiveness of your incident response plan can only be validated under fire.
You can start with preliminary testing, by consulting stakeholders such as your incident response team, or more likely that of your security partner, even your suppliers and your strategic customers, to discuss the plan and investigate various scenarios.
Actual testing should be done at least once a year and could include a phishing attack, ransomware attack, or denial of service attack.
It's the ultimate way to know if, and how well, your incident response plan is actually working.
Conclusion
Due to often insufficient security and personal data protection measures, SMEs are vulnerable and therefore targeted.
However, when a cybersecurity incident occurs, time is a key factor.
In this context, having a ready-to-implement response plan in place is the most effective way to reduce the costs and impact of a security incident,
According to IBM: “An effective incident response plan can help cybersecurity teams detect and contain cyber threats, recover affected systems faster, and reduce lost revenue, regulatory fines, and other costs associated with these threats."
To facilitate your approach, we can help you assess the maturity of your security posture and your incident response policies and identify areas for improvement.
We then present a document presenting the recommendations, the steps and the services that we propose, in order to make your environment more robust and to better respond to the incidents that are sure to occur.
Contact us to learn more about Incident Response as a Service.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

