Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
Multi-Factor Authentication: understand the risks, focus on quick wins, and act as soon as possible
present Groundhog day
Groundhog day
"Hackers Don’t Break In, They Log In."
Day after day, adversaries connect to their victims' services and applications using means such as:
- Stealing user credentials through phishing campaigns.
- Trying passwords from leaked datasets, in case a user has reused the same password on other services.
- Attempting to log in to multiple user accounts using one of the passwords on the most used password lists (password spraying).
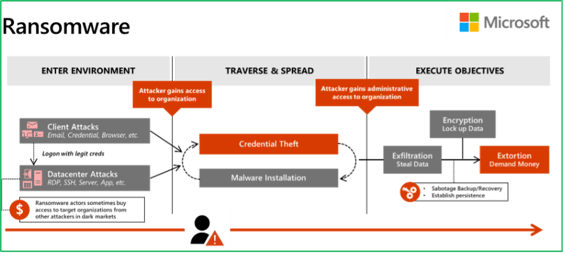
The goal
How can SMBs protect their critical data and personal information (Bill 64 compliance) against theft, malicious access, destruction, encryption and more broadly against downtime?
Make it harder for attackers by prioritizing quick wins
There are essentially 3 priority initiatives to put in place:
- Implement Double Identity Verification (MFA).
- Implement advanced security and manage endpoints (MDR).
- Protect your data and backup infrastructure.
Today we're going to focus on multi-factor authentication, keeping in mind an alarming disparity, as reported by Microsoft:
- Over 80% of data breaches are directly related to the misuse and theft of credentials.
- Less than 40% of companies have implemented multi-factor authentication.
The Colonial Pipeline example of what not to do
“The hack that took down the largest fuel pipeline in the U.S. and led to shortages across the East Coast was the result of a single compromised password… The VPN account, which has since been deactivated, didn’t use multifactor authentication, a basic cybersecurity tool, allowing the hackers to breach Colonial’s network using just a compromised username and password.”
– Bloomberg Cybersecurity “Hackers Breached Colonial Pipeline Using Compromised Password”
What is Multi-Factor Authentication
One of the most common ways adversaries gain access to corporate data is by guessing weak passwords or stealing them, whether through phishing or buying them on the Dark Web.
From there, they get the same permissions as legitimate users, including administrators and power users.
The goal of multi-factor authentication is to create an additional layer of defense beyond just using a password.
How Multi-Factor Authentication Works
Multi-factor authentication requires at least two independent pieces of information (2FA) to verify a user's identity when attempting to log in or access a resource.

For example, Azure AD multi-factor authentication requires at least two of the following authentication factors:
- Something you know, usually a password.
- Something you have, like a phone or hardware key.
- Something that you are, like a fingerprint or facial recognition.
Who does multi-factor authentication apply to?
Companies that purchase cyber insurance are no doubt aware of today's minimum requirements for multi-factor authentication.
Today to benefit from coverage it is necessary that MFA be applied at least to the following situations:
- Remote access (VPN, RDP, SSH and others).
- Administrative accounts and privileged access accounts.
- Email and collaboration platform such as M365.
It would also be appropriate to add multi-factor authentication to the backup solution.
Still, the best practice should be to implement MFA for all users, 100% of the time, especially if, as in the case with M365, companies can maximize features they already have with their plans.
Microsoft 365 Multi-Factor Authentication
There are several ways to enable MFA with M365, depending on the plans in use and the level of control and flexibility desired.
The table below provides a high-level overview. Legacy per-user mode is not mentioned, as it is being retired by Microsoft.
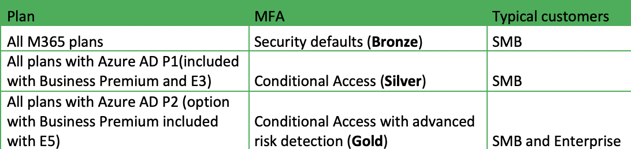
What to remember?
- Default security settings enable Microsoft Authenticator for all users, and provide a basic level of security.
- For more granular and comprehensive controls, and easy user acceptance, we recommend using Conditional Access policies to define events or applications that require MFA.
These policies can allow single-factor login when the user is on the corporate network and/or on a registered device, but require additional verification factors when the user is remote or on a registered personal device.
Conditional Access policies are based on "if-then" statements, as shown below.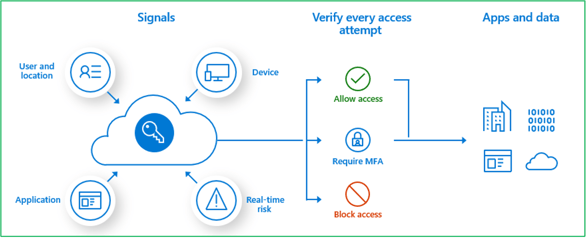
Conclusion
- Although multi-factor authentication is unquestionably essential to protect organizations against cyberattacks - especially ransomware - too many companies still rely on authentication based on the use of a simple password.
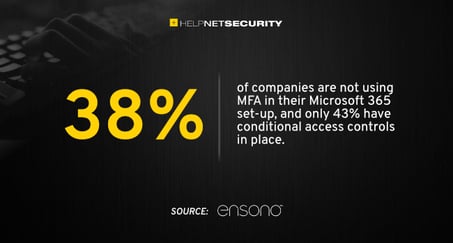
- In the case of M365, this means that companies are neglecting the vital cybersecurity functions available on the platform, which exposes them, unduly, to major vulnerabilities.
- This is why SMBs must act without delay to secure access to their resources using strong authentication, and thus achieve significant and rapid security gains, at a low cost.
As a Microsoft Gold Partner, our platform of choice for multi-factor authentication is Azure AD, which makes it very easy and integrated to meet different requirements, from the simplest (default security) to the most sophisticated (conditional access with or without integration with Azure AD Identity Protection included with Azure AD P2).
Deploying attack-resistant user authentication is the first initiative to put in place from a Zero Trust perspective.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

