Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 With the increasing sophistication and scale of ransomware attacks, hiding your head in the sand and hoping not to be among the victims is, without doubt, a doomed strategy.
With the increasing sophistication and scale of ransomware attacks, hiding your head in the sand and hoping not to be among the victims is, without doubt, a doomed strategy.
The situation
Ransomware is now more likely to strike your business than any other form of disaster and could, in fact, be more damaging.
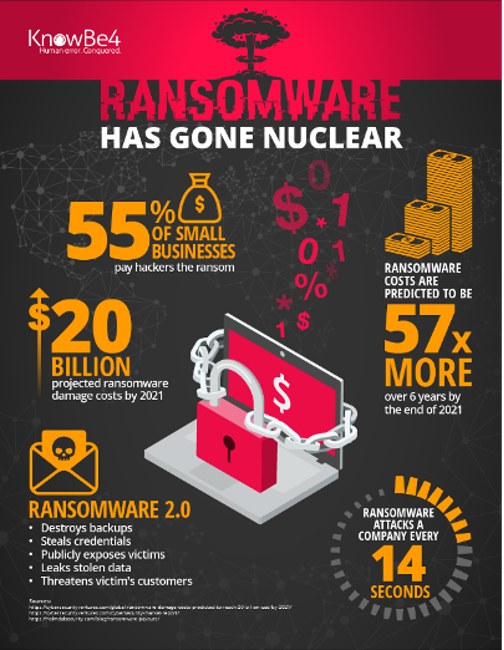
You need to assume that your company will be the victim of multiple attacks and be prepared for them.
It's a matter of choosing between two alternatives:
- Invest in a plan now and adapt your preparedness as time and the threat evolves.
- Pay a ransom, and experience more or less prolonged downtime and/or the slowing down of your systems, until you invest in a plan.
An irrefutable statement
- The reason enterprise ransomware revenues are growing so fast is because more and more companies, in all industries and sizes, are paying higher and higher ransoms.
- Why should you wait until you have an attack before you have a plan?
Why are so many companies paying the ransom?
Essentially three reasons explain the prosperity of cyber criminality:
- Victims have no choice but to pay, as their data AND backups have been rendered unusable. But even if victims do manage to decrypt their data, that doesn't mean they are off the hook, as they still have to invest weeks or even months of effort to make their systems fully functional.
- Paying a ransom is often the cheapest option. An example is a well-known Quebec company, which allegedly refused to pay the ransom, but then spent an enormous amount of money, compared to the ransom demanded, to respond to the attack that destabilized its operations.
- Victims are able to recover a lot part of their data from backups, but highly confidential data has been infiltrated. They must therefore pay the ransom in hopes that the information is not published on the Dark Web.
In reality, paying the ransom does not guarantee that you will be able to recover your data or that you will not fall victim to the same attack again, especially if you do not do a thorough analysis to determine how the cybercriminals infiltrated the network.
In addition, you will most probably need to reinstall all of your applications if you are not sure you can eradicate the threat. And it is common to see that it will then take several months to get back to normal thus increasing the real cost of the ransom.
In any event, if we are not careful, paying ransoms risks becoming an operating cost just like paying for electricity.
This is somewhat reminiscent of the protection that traditional thugs offering their victims.
3 examples of how current ransomware works
Today's ransomware is much more sophisticated than its predecessor.
New versions appear without being detected by the most common traditional antiviruses, since they operate based on the recognition of a static signature.
- Instead of encrypting as many files as possible as quickly as possible, they can remain inactive, and be backed up multiple times, so that they are activated during a restore.
- Or the ransomware may initiate the encryption process slowly to avoid being detected. In some cases, it first encrypts files based on the last access date, starting with the oldest data and then working its way to the most recent files.
- In other cases, ransomware can specifically target file extensions corresponding to backup software.
What are the vectors of attack?
To counter the threat, you need to know how ransomware can infect your systems. These methods of accessing your systems are known as attack vectors. Here are a few.
How to defend against this threat?
According to George Washington, "Preparing for war is the best way to preserve the peace".
So, of course, it is vital to put in place a protection respecting the best practices.
How to recover after a successful attack?
The ideal is to prevent the ransomware attack, as recovery can be arduous, complex, time-consuming and expensive, even if you have clean and recent backups.
But even if you take all the necessary precautions to protect your business, you still risk falling victim to a successful attack.
The specifics to be taken into account in terms of recovery are as follows:
- Usually a recovery plan aims to recover from the loss of the data center. The special thing about ransomware is that the data center as such is still functional, but you can no longer access all or part of your data.
- Your backup site may also be infected or vulnerable to infection, you must contain the ransomware attack before performing a recovery.
- Some backups may have been encrypted and therefore not usable unless you have immutable copies.
- Immutable copies cannot prevent backing up corrupted files or ransomware ready to detonate on recovery.
You must therefore have a specific ransomware recovery plan in place and have the practice to enable you to execute it properly.
Elements of a recovery plan
In the case you are under fire from a successful ransomware attack, the highest priority actions are containment.
Preparation
This phase is to prepare your business for the ransomware attacks it may experience. It includes, but is not limited to, the application of the best practices mentioned above. It's about establishing and implementing your ransomware prevention checklist.
Detection
The way a company detects a ransomware infection can vary depending on the situation, but in most cases an employee is unable to access files or notices that certain services are no longer accessible.
The urgency then is to identify all infected systems and those in imminent danger of being infected.
Analysis
The analysis phase essentially focuses on two aspects:
- Identify the specific variant of the ransomware in action
- Determine how the ransomware entered the business (root cause analysis)
Containment
The containment phase is an essential element of the response plan. Once a system has been identified as potentially containing ransomware, the computer suspected of being infected should be immediately removed from your networks, and either shut down or ideally put into hibernation to aid in analysis, while minimizing the risk of the ransomware continuing the encryption process.
Eradication
The eradication phase involves removing the ransomware from infected systems across the enterprise. Depending on the extent of the attack, this operation can take a long time and can affect both user devices and servers that have been affected.
It should be noted that in most cases, reinstallation of the contaminated servers or workstations is required.
Recovery
Once a business has contained the ransomware and identified the root cause of the infection, there are several considerations that a business should consider when entering the recovery phase.
Post mortem review
A post mortem review is an important part of the response plan and should not be overlooked. After any incident, large or small, it is recommended that you meet with relevant stakeholders and discuss what worked well and review what did not.
This type of analysis can help your business improve processes over time and ensure that future incidents are handled more effectively, and therefore minimize the potential impact.
Recommendations
You can't prevent ransomware attempts, but you can greatly reduce your exposure to risk and develop a plan to deal with it.
- There is not a miracle measure, but rather a coordinated set of measures including:
- Raise awareness and train users
- Protect endpoints including servers using behavior analysis, rather than signatures, so that previously unknown malware can be detected
- Set up a reliable backup process based on best practices
- If you haven't already implemented ransomware prevention best practices, now is the time to do so.
- Finally, it is imperative to practice your plan.
Contact our IT security experts, they will be able to offer you the best cybersecurity advice and solutions for your business.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)


