Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
Datto SIRIS: The All-In-One Managed Continuity Solution, with Native Immutability
present For adversaries, it is no longer just a matter of encrypting backups and production data. It's also about stealing your data in order to sell it, and, to add insult to injury, to carry out denial of service attacks. This approach of coercing you into paying the ransom is referred to as triple extortion.
For adversaries, it is no longer just a matter of encrypting backups and production data. It's also about stealing your data in order to sell it, and, to add insult to injury, to carry out denial of service attacks. This approach of coercing you into paying the ransom is referred to as triple extortion.
The objective of Ransomware as a Service is obviously to maximize the return on investment of attacks, which today we know massively target SMBs. The reason being they are the most numerous and the least well protected. In short, they are the ideal prospect for this criminal industry.
A critical mission for SMB leaders

Make the opponent's attack "more expensive"
The table below summarizes the ins and outs of an attack.
More specifically, in the right column, are the basic measures to be put in place in order to prevent and detect threats, and enable a return to normal in the case of an attack.
|
Consequences of a Ransomware Cyber Attack |
Main attack vectors |
Gain visibility; classify the risks by importance, and act as quickly as possible |
Make it harder for attackers while prioritizing quick wins |
|
|
|
|
Backups under attack
Are you someone who thinks that simply having backup copies protects you from ransomware?
Unfortunately this is not always the case since adversaries seek primarily to make them inoperative, by destroying them or by encrypting them. The Conti ransomware group specializes in this practice.
You must been conscious that being able to restore does not protect you from the theft and resale of your data, or from denial of service attacks.
To protect yourself against data theft, you ultimately need to encrypt your data, and to counter denial of service attacks, it is necessary to put in place measures such as a web application firewall (WAF).
The fact remains that since your backup is your last line of defense, it must imperatively be able to counter hackers and ransomware.
Essentially your ability to recover backup copies is a function of the following factors:
- The guarantee of having a clean backup copy
You should use best practices especially those associated with the recommendation of immutability and integrity checking of backup copies known as 3-2-1-1-0 (3 copies (original + 2 backups), 2 storage types including 1 offsite copy, immutable (1) and error free (0)). - The freshness of your data or RPO (Return Point Objective)
You should be able to take copies in short intervals without a penalty on your production applications. - Return to production time or RTO (Return Time Objective)
Whether on-premises or in the cloud, in the event of a site disaster, you should be able to get back to business without delay. - Access control
The administration of backup solutions being very sensitive, you should be able to validate and manage access in a very secure way. - Backup tests
You should be able to test your backups several times a year.
Datto SIRIS in action
The Datto SIRIS solution is a managed or co-managed business continuity service that combines all data protection elements into a single fully integrated service, to greatly simplify implementation and support.
It includes on-site equipment (appliance) that replicates backups in 2 geographically separated clouds in Canada as well as the required services.
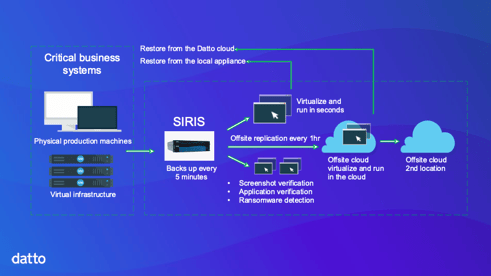
The guarantee of having an integrated backup copy
The solution relies on snapshots of the appliance file system so that all local and cloud backups are read-only. This means that they are immune to any type of modification, including ransomware infection. All backup copies are kept in private, secure clouds and may also use encryption.
Verification of backups for reliability of data recovery
SIRIS includes two levels of backup verification. Level 1 verification ensures that the system can boot, while Level 2 verification ensures that the systems are actually accessible. Additional reliability is provided by the integrated ransomware scan.
The freshness of your data and compliance with RPOs
Since the solution relies on snapshots rather than traditional copies, you can make copies at a frequency of 5 minutes rather than once or twice a day.
This means that during a local or remote restore, your loss of data (RPO) is minimal.
Time to return to production and compliance with RTOs
Entire systems can be restored in minutes with Datto's instant on-premises or cloud virtualization, while enjoying 5-minute data freshness.
Access control
The solution integrates many security features such as mandatory two-factor authentication, as well as the management and monitoring of active sessions.
Backup tests
Present, in conjunction with Datto, recommends carrying out 4 recovery tests per year.
Conclusion
Datto SIRIS is a fully integrated and managed service, payable on a monthly basis, which makes it the ideal solution for SMBs in these troubled times.
Datto SIRIS includes:
- Protection of backups against ransomware;
- The managed backup and continuity service respecting a RTO and RPO of a few minutes;
- Backups replicated in the Datto cloud;
- Increased security thanks to a third backup in a second cloud with even more restricted access;
- Unlimited cloud retention;
- Local and disaster recovery (DR) in the Datto cloud;
Datto SIRIS meets current continuity requirements namely:
- Facilitate the response to threats associated with backup copies;
- Apply best practices including immutable copies of data;
- Reduce or free yourself from the burden of business continuity management;
To ensure you successfully complete your mission, schedule a demo to see how quickly you recover from a ransomware attack with the Datto solution. Or join Present and Datto's webinar on Apri 21st at 11am, where we will simulate a cyberattack and then demonstrate how the business continuity solution can literally save your business in the event of a cyberattack or outage. The webinar will be given in French.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)


.png?width=600&name=Datto%20invitation%20header%20(4).png)