Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
Why it's time to break up with your antivirus and adopt an MDR service
Benoit Mercier_ Every day thousands of endpoints are compromised by cybercriminals, whether they are beginners or professionals. These cybercriminals use techniques to bypass antivirus software that historically only compared the signing of files to a database of known malicious files. This also means that any new strain of virus will strike hard before it is recognized, analyzed and then passed on to all antivirus vendors for blocking.
Every day thousands of endpoints are compromised by cybercriminals, whether they are beginners or professionals. These cybercriminals use techniques to bypass antivirus software that historically only compared the signing of files to a database of known malicious files. This also means that any new strain of virus will strike hard before it is recognized, analyzed and then passed on to all antivirus vendors for blocking.
This is not the only weakness of these antiviruses; indeed to be able to compare the signature, a file must be deposited. However, many techniques exist to overcome this obstacle and perform malicious actions directly in memory, we speak here of "fileless" attacks, because they do not drop files, but execute code directly in memory.
Regardless of these advanced threats, antiviruses miss a crucial point in today's security environment - that of correlation. We study and analyze the attacks endpoint by endpoint without a global visibility. It is complex and time consuming to find the original path of infection.
Nevertheless, antiviruses, and in particular the "next gen" which do more than just compare files, still make it possible to block a large amount of malware. But this is no longer enough to be well protected.
EDR, MDR, SOC ... important acronyms
The cybersecurity market has seen the emergence of new EDR (Endpoint Detection and Response) type offerings. These are based on agents installed on the endpoints. They collect and send behavioral data to a central database for analysis. They are then able to identify trends and detect anomalies, which can then be automated to send alerts for corrective action or further investigation.
EDR software will generate alerts that need to be dealt with quickly. Some will be real malicious behavior, while others will not be so clear and will require investigation. This is where the SOC (Security Operations Center) becomes relevant. SOC is a business unit of security experts responsible for ongoing security oversight.
When an EDR is managed externally by a SOC, this is referred to as an MDR (Managed Detection and Response) service.
It is therefore a turnkey protection solution to adequately protect your endpoints from multiple vulnerabilities.
Threat protection tailored to today's threats
Faced with ever-growing cybersecurity vulnerabilities and threats, it becomes imperative to take the means to protect yourself and thus enhance your security posture.
As we are increasingly in a decentralized world, with remote work and cloud services, the network protection approach is still relevant, but remains very incomplete. Only endpoint-focused protection can adequately protect you.
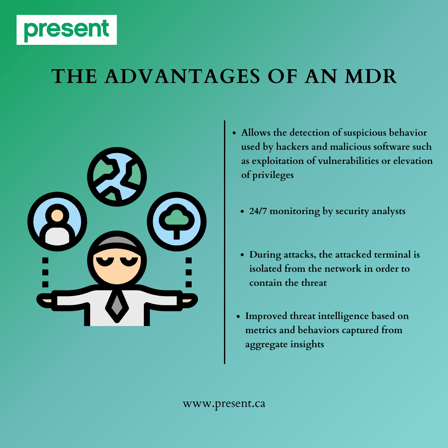
An MDR service protects your endpoints far beyond what a simple antivirus can do. It provides the following advantages:
- Allows the detection of suspicious behavior used by hackers and malicious software such as exploitation of vulnerabilities or elevation of privileges
- 24/7 monitoring by security analysts
- During attacks, the attacked endpoints is isolated from the network in order to contain the threat
- Improved threat intelligence based on metrics and behaviors captured from aggregate insights
Convinced of adopting an MDR? Great news as we have a team of cybersecurity experts with a well-established MDR service at your disposal so that you can focus on the success of your business with peace of mind.
Complete this form to receive a quote within 24 hours and learn how to ensure the highest possible level of endpoint protection for an affordable monthly rate.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

