Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
Why Dark Web Scanning is a crucial element to a solid cybersecurity strategy
Jennifer Bridgeman Many organizations are not aware of the dark web and its dangers. Others don’t think it is a threat to their organization. But what you don’t know can hurt you.
Many organizations are not aware of the dark web and its dangers. Others don’t think it is a threat to their organization. But what you don’t know can hurt you.
According to Visual Capitalist, the “surface web” represents only 4% of the internet. It is the portion of the internet that is indexed by search engines and can be traced easily.
Dive deeper and you find the deep web which makes up most of the internet. Search engines don’t index those sites, but you can access them from a standard web browser.
Then you have the dark web, representing only a tiny percentage. The Dark Web is a nefarious part of the Deep Web: an obscure sub-internet designed to house illicit databases and provide anonymity to criminals.
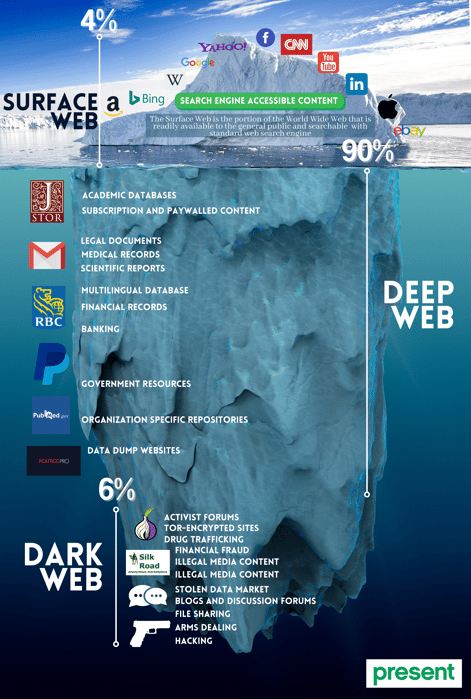
We don’t need to know the ins and outs of the dark web, but it is important to understand the risk the dark web poses of a data breach and how incorporating dark web monitoring into your overall cybersecurity strategy is important.
Today’s hackers are working smarter, not harder and have all sorts of strategies for finding valid credentials that give them access to a corporate network or company data. These strategies include phishing, malware, social engineering, exploiting known vulnerabilities and they also use the dark web to buy what they want.
Research finds that most breaches are not initially detected and may not be discovered until several months after the initial attack. According to IBM’s Cost of a Data Breach Report 2020, the average time to identify and contain a data breach is 280 days (approximately nine months). Often, breaches are only detected after it is discovered that compromised, sensitive information has been released or is for sale on the dark web. Are any of your corporate credentials for sale on the dark web?
A dark web scan can help further identify risk exposure and act as an early warning to potential dark web risks. It can also protect employee credentials. The scan can uncover any exposed employee credentials and allows you to set up ongoing monitoring so you will be notified of any future credential leaks.
What to Do When Your Credentials Have Been Exposed?
Running a dark web scan against an email domain can provide eye opening results. For example, one organization’s email domain scan uncovered 30 compromised emails, including the business owner’s bank account login credentials. And this is just one example, we’ve seen many shocking results running these reports for clients.
Brush Up on Password Best Practices
If your credentials have been exposed publicly, you can never use that password again. Once that password is part of a public list, especially one that is associated with your email address, you can be sure it will be used in a future attack. The risk is too great to even consider using it again, and any other account that uses the same password should be immediately changed as well. Similar passwords used with other accounts should be changed too.
Business email addresses should NOT be used for non-business-related activities, and separate passwords should be used for each site or application you use. The results of a dark web scan will show if any of your employees may have used their business email for non-business reasons and had their credentials compromised, bringing unnecessary risk to your organization.
If you identify any of your users’ credentials for sale on the dark web, take the necessary steps to remediate the situation.
The Bottom Line
A dark web scan can be used as an early warning tool and is one more way to understand the strength of your current cyber defence. The next step is to prioritize strengthening your security posture for the future. That includes training your users on their role in defence of the organization, setting up multi-factor authentication (MFA) and employing an MDR service to secure your endpoints so you will be alerted if (or rather when) an attack is attempted.
There’s No Better Time to Find Out
Many organizations are shocked and surprised when they see their employees’ access information available for sale on the dark web. Whether you have a large enterprise or a small- to mid-sized business, be sure you aren’t a target!
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

