Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 We all know that security is a top priority for businesses. In fact, we see in AXA’s latest Future Risk Report 2021, that cybersecurity risks rank second globally, only after climate change as the main risks in the next five to ten years.
We all know that security is a top priority for businesses. In fact, we see in AXA’s latest Future Risk Report 2021, that cybersecurity risks rank second globally, only after climate change as the main risks in the next five to ten years.
We also know that not all organizations are fortunate enough to be familiar with their vulnerabilities against different types of cyber-attacks. Knowing where you are at is imperative to protecting your business. This is why a security audit can be a powerful tool in your organization and is an essential first step.
But what exactly is a security audit?
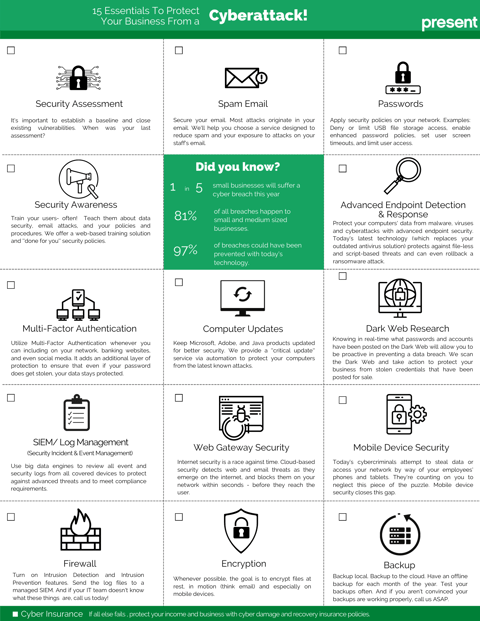
A security audit is a thorough assessment of the security of a company's information systems by measuring its compliance with a set of established criteria. A thorough audit typically assesses the security of the physical configuration and environment of the system, software, information handling processes, password policies, backup strategies and user practices.
The physical part of an IT security audit in which the auditor verifies physical hardware access for security and other administrative issues is important but, in this article, we will only be covering the non-physical part.
There are three main components that are covered in an IT security audit.
1. Network Analysis
The network analysis provides visibility into the environment and makes it possible to present an analysis of the overall risk score concerning, in particular, the following points:
- Inactive computers
- Password strength analysis
- User password set to never expire
- Anti-spyware not installed
- Antivirus not installed
- Unsecured listening ports
- Missing security updates
2. IT Systems analysis
This analysis Integrates and complements the network analysis through the use of additional specialized tools for vulnerability detection. You will get a better understanding of your risks related to items such as:
- Active Directory and Azure / Office 365
- Availability of passwords in the Dark Web.
- Backup strategy
- The various internal vulnerabilities
3. Penetration Testing
In this type of audit, security experts will simulate attacks to identify the weak spots in your system’s defenses which attackers could take advantage of and plan corrective actions.
- The external penetration test simulates an attacker outside your security perimeter.
- The internal penetration test simulates an attack from an employee or partner.
- There are also penetration tests for web server, and cloud services
The benefits of a security audit
A security audit will provide a roadmap of your organization’s main IT security weaknesses and gaps in compliance as well as provide access to the tools and training to remedy the situation.
There are several reasons for carrying out a security audit:
- Identify security issues and gaps, as well as system weaknesses.
- Establish a security basis against which future audits can be compared.
- Comply with the organization's internal security policies.
- Comply with external regulatory requirements.
- Determine if the safety training is adequate.
- Identify unnecessary resources.
- Identify shadow resources (Shadow IT)
Security audits help protect critical data, identify security vulnerabilities in your system, create new security policies, and monitor the effectiveness of security policies. Regular audits can help ensure that employees are using security practices and can detect new vulnerabilities.
The best intervention is prevention, and that starts with an IT security audit.
To learn more about Present’s security solutions, please visit our website.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)