Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
Protect yourself now, thank us later
 Remote working for most businesses has been set up for more than a year now, pleasing many cybercriminals. In fact, we see that hackers have taken advantage of the fact that a majority of us are working remotely to defraud companies around the world, and Quebec is no exception.
Remote working for most businesses has been set up for more than a year now, pleasing many cybercriminals. In fact, we see that hackers have taken advantage of the fact that a majority of us are working remotely to defraud companies around the world, and Quebec is no exception.
In 2020, approximately 61,000 SMEs were the target of cyberattacks. So, it's not whether your business will be a victim, but rather when. “Since 2019, ransomware has increasingly been used to attack large businesses or organizations. Hackers carry out a three-phase attack to infiltrate computer networks and encrypt all the data on them. They then demand a large sum from the administrators, in return for which they usually release the data. '' According to a PwC investigation, the increase in online activity due to COVID-19 has made cyberattacks the main threat to the growth potential of organizations in North America last year.
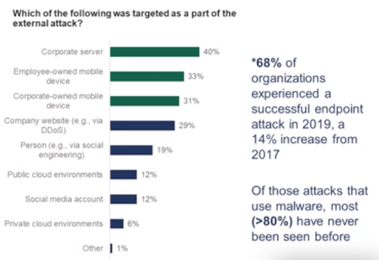
It all starts with Endpoints
With all its predisposition, it is easy to see that endpoints (servers, networks, workstations) are the easiest points for cybercriminals to enter companies. So how can you protect yourself against these growing threats?
Traditionally, antivirus software was enough to protect enterprise endpoints. But in today's world, it is imperative for companies to implement an EDR (Endpoint Detection and Response) solution. Endpoint threat detection and response (EDR) solutions are effective in protecting your business and its endpoints.
Let's see how this solution works. And how it differs from traditional antiviruses.
The process is similar to a traditional home alarm system. Obviously, everyone knows how important it is to install one to protect your home. But what happens if your alarm system (traditional antivirus) is not connected to a security center? It may ring the bell to warn that someone is trying to enter your home, if no one is notified in time, can it really prevent the intrusion? This is where the big difference between antivirus and SOC solution lies: the notion of "real time."
This principle applies for the protection of your IT environment. By installing agents on endpoints, it helps to collect, analyze and detect threats to network's behavior, using artificial intelligence and machine learning. While the traditional antivirus will detect the virus, it will not detect the malicious action that is taking place until the action is irreversible. Plus, knowing that malwares are constantly evolving, and that antiviruses stop only those they know, it is often too late when a company realizes they have been attacked. If the antivirus does not know "the definition of virus", it will not be able to stop it.
The Real Case of a Cyberattack at Our Client
One of our clients was the victim of a cyberattack attempt last month. They came close to losing their entire business. Fortunately, this situation was avoided, thanks to our SOC offering which includes an EDR solution. Let's take a closer look at the situation.
Threat Detected - In-Depth Analysis - Threat Overview and SOC Action
Our threat detection agent had been in place for a few months on each of our client's computer workstations and servers. This agent performs continuous analysis of data since its installation, using numerous artificial intelligence algorithms.
An employee of the company in question used his personal computer, which is connected to the VPN, to do some work and send some emails. As he finished his day, he left his computer in the office and headed for the kitchen. Meanwhile, his child took the opportunity to do his homework on the computer in question and to play games on the internet. Then, at the end of the evening, he leaves the office, without shutting down the computer.
36 Attacks Blocked in Record Time
In the middle of the night, something abnormal happened on the client's terminal server and the malicious action was identified. The agent spotted 36 simultaneous attacks. He noticed that one of our client's users has connected to the network on his home computer at 3 a.m. and was trying to send commands to other remote server stations; he was also asking to elevate his access rights. The behavioral analysis done by artificial intelligence immediately identified this action as malicious.
Within a few seconds, an alert is automatically sent to our SOC team, which is on duty 24/7, to recheck whether the action taken by the user is indeed a malicious anomaly or if it is a false positive. In the meantime, the potentially infected endpoint is traced, the 36 simultaneous attacks are immediately stopped, and the workstation is quarantined. With the attack confirmed, our SOC team continues to analyze and investigate to ensure that everything is back to normal and that there is no threat to the customer. Once the environment is secure, our team calls the client to inform them of the situation. He hadn't even realized he had been the victim of a cyberattack. Fortunately, thanks to our security solution, the client avoided what every business fears: the loss of its data.
Conclusion
Take action before it is too late, and your business is yet another victim of ransomware by requesting an assessment of your IT environment. Our solution, which is a pay-as-you-go monthly model, deploys quickly and immediately protects you against cyber-attacks. So, what are you waiting for?
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)


