Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 The main goal of cybercriminal organizations and independent hackers is to access your data in order to hold it hostage and to steal it.
The main goal of cybercriminal organizations and independent hackers is to access your data in order to hold it hostage and to steal it.
And the endpoints (your computers) are the primary gateways to a wider network penetration, which includes internal and external servers, email, the cloud, and anything of monetary value to them.
What is a ransomware?
According to James Scott, author of The CEO’s Manual on Cyber Security: "Ransomware is a particular cybercrime, since, for an attack to be successful, the victim must be an accomplice after the fact."
Given the large number of attacks that have hit the headlines lately, it is common knowledge that a ransomware is a malicious software that aims to hold your data hostage for ransom. The criminals then promise to release it in exchange for paying a ransom, usually in bitcoin.
Otherwise, they threaten to destroy that information permanently, disclose it to the public, or sell it on the dark web.
Who are the targets?
Any business can be a target for ransomware. No industry or sector of private or public activity, or company size, is immune to this type of attack.
In recent times, a growing number of Canadian businesses have fallen victim to cyber ransomware attacks.
Studies show that over 50% of SMBs pay the ransom, sometimes twice, first to free their data, and second to erase data that was stolen.
In other words, ransomware is the number one security threat that companies face. This is particularly the case for SMBs which generally do not have the necessary resources to effectively combat this threat.
How big is the threat?
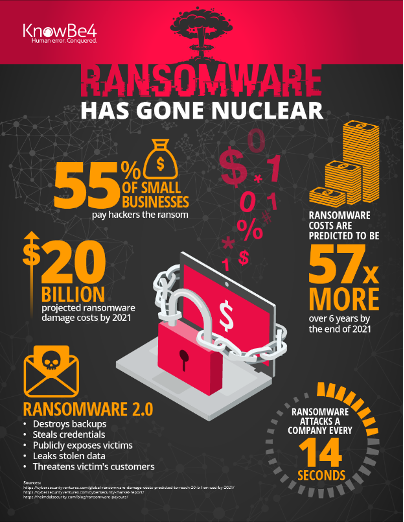
Some notable statistics and observations on the current state of ransomware include those provided by KnowBe4:
- 55% of SMBs pay ransom to hackers
- The cost of ransoms is expected to be 57 times higher over a 6-year period by 2021
- New strains of ransomware include:
- destroying backups
- stealing identities
- publicly exposing victims
- disclosing stolen data
- even threatening the victim’s clients
Ransomware has become the attack you wouldn't wish on your worst enemy.
What are the vectors of attack?
To counter the threat, you need to know how ransomware can infect your systems. These methods of accessing your systems are known as attack vectors. Here are a few.
- Phishing - The most common method for hackers to initially infect an endpoint with ransomware is through phishing emails. Increasingly targeted, personalized and specific information is used to create emails intended to gain trust and trick potential victims into opening attachments or clicking links to download PDFs and other malicious documents.
- Social engineering - The criminal can impersonate the company’s IT support and ask a user to log in remotely to do an update. In reality, the perpetrator could, at the time of the remote intervention, either deactivate the defences of the workstation or even hide and execute malicious code.
- RDP (Remote Desktop Protocol) — Criminals take advantage of the fact that IT administrators sometimes open the RDP ports of servers or workstations directly to the Internet. Attackers will then attempt to find the password for the IT equipment, which is easier when passwords are weak. They then use these machines as a point of support to detect the credentials of the domain administrator.
Attackers therefore use all the means at their disposal to infiltrate the company and install malware and thus compromising their targets.

How to protect against this threat?
Of course, it is imperative that you apply best practices such as:
- Raise awareness and train users;
- Secure your VPN and RDP using two-factor authentication;
- Limit user access rights to computer systems and data;
- Control privileged access and analyze their use;
- Regularly update operating systems and applications;
- Secure the back-up infrastructure;
- Observe the 3-2-1-0 rule and use immutable storage;
- Take out an insurance contract against cyber risks.
But it’s obviously always better to prevent a ransomware attack, as recovery can be arduous, complex, time-consuming and expensive, even if you have clean and recent backups.
After all, why take medication after the fact, when you can get the vaccine?
However, the situation of companies, more specifically, that of SMBs is as follows:
- As new threats can no longer be identified by traditional antiviruses, they are not able to detect them.
- Their teams do not have the time, capacity or expertise to develop all the solutions required to respond to increasingly sophisticated threats.
- The costs of monitoring, analyzing and responding to incidents and endpoint attacks prevent their teams from focusing on strategic priorities.
- They are at risk of interrupting their operations for several days or even weeks.
- They risk the exfiltration of personal data of partners (customers, suppliers, employees) and of its assets that can be resold on the underground Internet
This is where Present’s Managed Security Service really makes sense.
Present Managed Security Service
The managed services for endpoint protection unifies detection, prevention and response.
As soon as a malicious behaviour is identified by the agent who uses artificial intelligence and automation, the service triggers a set of measures that immediately neutralizes the attack, with the following benefits:
- Risk Mitigation - Easy-to-configure rules allow you to stop suspicious processes, and either quarantine them, or delete malicious files and all associated items before potentially isolating the equipment from the rest of the network.
- Immunization - As soon as an attack is blocked, relevant information is immediately shared with other network equipment to immunize systems that may be targeted in a coordinated attack.
- Fix - Deleted or modified files are automatically restored to a pre-attack state.
- Active threat monitoring - this is performed by a team of experts 24/7, to compliment automation, and is an integral part of our service to optimize protection against endpoint cyber attacks.
In addition to our core service, which is focused on protecting endpoints, we also offer an extensive range of security services.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

