Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 Ransomware has become the top security concern for all organizations, regardless of size.
Ransomware has become the top security concern for all organizations, regardless of size.
This is because adversaries have a wide range of methods at their disposal to deploy and install ransomware.
In this context, the preventive approach adopted by SMBs consists of a number of best practices such as:
- Educate users about security and phishing;
- Replace antivirus with EDR (Endpoint Detection & Response) tools;
- Secure the identities associated with VPN/RDP, administrative access, emails and more broadly for all users;
- Manage security patches;
- Implement the principle of least privilege, which states that employees should only be granted the access and permissions required for their job;
- Segment the network to limit the spread of attacks.
But is it enough?
As cyberattacks and threats become more frequent, sophisticated and high-profile, many SMBs realize they now need real-time, proactive detection, alerting and response defensive capabilities.
SMBs, who are paying an increasingly heavy price to adversaries, are realising that the type of prevention usually implemented is no longer sufficient in the face of current threats.
The risks they are incurring make a defensive posture unsustainable, therefore SMBs have no choice but to combine prevention and defensive capacity in such a way as to improve their response capacity.
According to the Cost of Data Breach Report, it takes an average of 280 days to identify and contain a security incident. Being able to reduce this time also means minimizing risk and costs.
EDR and SOC
For example, in the context of endpoint protection (workstations and servers), as indicated above, the legacy antiviruses of the past are replaced by EDR tools.
But at the same time, to be fully effective, the EDR tool must absolutely be managed by a team of experts and managers overseeing security operations.
This team forms the SOC (Security Operations Center), and in an EDR context, ensures endpoint security through 24/7 monitoring and alert handling.
When the EDR tool is managed by an SOC, it is then referred to as a MDR (Managed Detection and Response) service.
Gartner's Trinity
But of course the SOC service is not limited to EDR tools. We should also mention SIEM (Security information Event Management) and NDR (Network Detection and Response).
Along with the EDR tool, these are the 2 elements of Gartner's SOC visibility trinity.
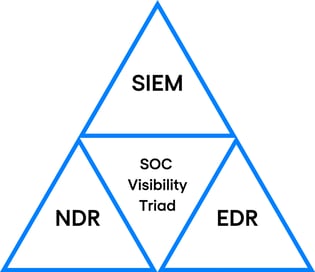
Used in conjunction with preventative measures, these defensive technologies monitored by the SOC provide robust protection against ransomware attacks.
Managed EDR tools and intrusion prevention systems (IPS) can help detect and block malware infections, while SIEM solutions provide crucial visibility for rapid incident response.
SIEM solutions can be configured to collect data from the firewall, EDR tool, IPS system, operating systems and more broadly any other system or application that has event logs.
That being said, it is therefore a question of making the choice between an internal SOC and a SOC-as-a-service.
Why a SOC-as-a service rather than on-premises
The main reason to choose the SOC-as-a-service option is that it is not necessary to set up a SOC, since it is provided as a service. This means that you do not have to choose the technology, nor hire a team of specialists that you will first have to find and then manage and train. Additionally you don't have to set up the associated processes.
Conclusion
Generally, companies tend to be more reactive rather than proactive. This creates a vulnerability that adversaries take advantage of.
This is why the SOC, which aims to monitor, detect and analyze security threats in real time, is so important.
SOC as a service is unquestionably the winning option for SMBs.
To learn more about Present’s security solutions, please visit our website.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

