Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 When it comes to successfully protecting your business' infrastructure, you know it requires the use of multiple solutions which, when effectively integrated, creates a comprehensive, multi-layered defense in order to protect you from malicious intrusions within your network.
When it comes to successfully protecting your business' infrastructure, you know it requires the use of multiple solutions which, when effectively integrated, creates a comprehensive, multi-layered defense in order to protect you from malicious intrusions within your network.
When reviewing different cyber defense solutions, the positioning of Endpoint Detection and Response (EDR) versus Security Information and Event Management (SIEM) may be raised, primarily because each solution makes it possible to better secure your environment.
But is only one of these systems needed? Are they mutually exclusive?
Different solutions for different interventions
EDR and SIEM are designed to serve different purposes.
The main purpose of a SIEM is to provide information by collecting event logs (syslogs). By using a SIEM, you will be able to aggregate data within your company from various sources, including user workstations, web applications, physical and virtual servers as well as network devices, allowing you to consult millions of events in seconds.
In addition, a SIEM can generate high-context alerts, allowing actions to be taken that reduce the vulnerability of your environments.
An EDR on the other hand has a different set of capabilities. It is designed to provide continuous endpoint detection and response (endpoints - workstations, laptops, servers) against malware and threats and thus provides anti-ransomware capabilities.
The EDR comes by default with a set of behavioral detection rules and provides systems protection from day one. In addition, an EDR supports custom rule mechanisms and most EDRs provide detection based on artificial intelligence to counter emerging threats.
The house analogy
To illustrate how the use of a combined EDR and SIEM works we can use the analogy of a house with an alarm system and a camera system.
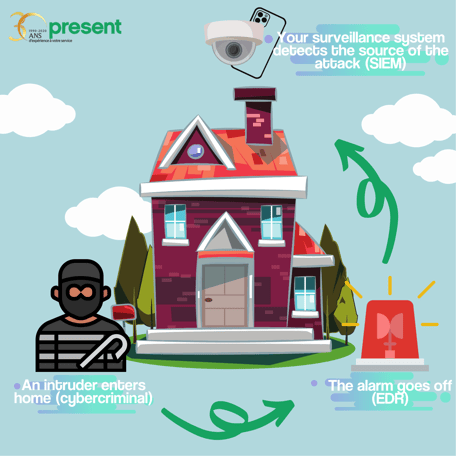
An EDR acts as a motion detector connected to a central. Should an intruder enter the house, the EDR will detect it, limit its actions and notify authorities, while preventing it from wreaking havoc. However, the EDR alone will not be able to explain how the intruder got into the house.
A SIEM acts as an advanced monitoring system with the ability to provide all the information about what has happened in its environment. In our analogy, the SIEM will be able to explain how the intruder entered (by the front door, the garage, the patio door or by any other means), what he tried to do, the paths traveled, etc. . Finally, the information from the SIEM will allow measures to be put in place that will increase security (in our example, some doors could be reinforced).
Therefore, a SIEM has a way of explaining what happened and doing prevention, but it's the EDR that stops the attacks!
To summarize
An EDR detects suspicious activities that are performed in systems and stops operations that could put your organization at risk.
A SIEM gathers all internal and external logs and analyzes them in order to take the appropriate actions to establish better security.
Used together, they can better protect your environment, better understand what attacks are being carried out against you, and take corrective actions to eliminate security holes in your business.
The protection and traceability capacity of these tools may be part of the compliance standards for your industry. This is the case, for example, in the field of pharmaceutical research and development.
For more information on our IT security offering, visit our website and request a meeting with one of our security experts by clicking on the link below.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

