Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 Companies have until September 22, 2023 to comply with the provisions of Bill 64. Failure to do so could expose themselves to criminal penalties of up to $ 25 million or 4% of their global turnover.
Companies have until September 22, 2023 to comply with the provisions of Bill 64. Failure to do so could expose themselves to criminal penalties of up to $ 25 million or 4% of their global turnover.
However, a recent FCCQ survey shows that 4 out of 10 companies do not understand the effects of Bill 64 on their activities, in a context where most companies only have a low level of maturity regarding data confidentiality management.
The context of Bill 64 (PL 64)
It is still fresh in Quebec's mind the massive theft of data of members of the Mouvement Desjardins, which demonstrated the consequences of negligent management of personal data.
Legislators certainly had this breach in mind when adopting Bill 64 on September 21, 2021, which modernizes the provisions applicable to the protection of personal information.
The law, inspired by the GDPR (General Data Protection Regulation) of the European Union, applies to any private or public company, within the meaning of the Civil Code of Quebec, which collects, holds, uses or communicates personal information.
Gradual but demanding adoption
According to the timeline below (available in French only), companies have until September 22, 2022 to appoint a privacy officer and have a privacy incident response plan.
They have until September 22, 2023 to adopt and disseminate a data governance policy, and until September 22, 2024 to comply with data portability, thereby allowing customers to retrieve their personal information.
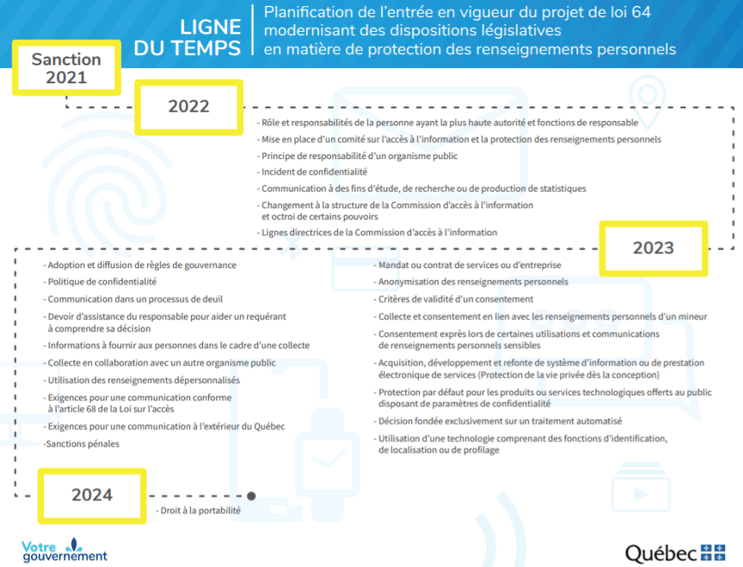
The risks of penalties applicable in 2023 are now forcing companies to answer the following questions:
-
What is our current situation in terms of the protection of personal information?
-
What actions will we need to take to ensure our business is in compliance?
-
Since compliance gaps can be significant, and therefore long and complex to close, when are we going to launch the project?
-
And so, are we going to take the cautious approach of the tortoise, the hasty approach of the hare, or worse, the elusive approach of the ostrich?
And now what?
You should adopt the tortoise strategy right away, because the road could be long, and the tasks and interdependencies too numerous for you to be able to skip any steps.
To be able to identify the changes you need to make and the resources you will need, you could take an approach that can be summarized as follows.
Plan
- Validate that Bill 64 applies to the activities of collecting and processing personal information by your organization.
- Understand the requirements of the law.
- Perform an analysis of your practices in terms of personal information management.
- Identify gaps and create privacy policies.
- Create your roadmap.
Deploy
- Appoint a person responsible for the protection of personal information.
- Create agreements with third parties concerned by your protection of personal information.
- Make your internal controls compliant.
Monitor
- Train your employees in best practices.
- Follow each step closely.
- Perform a privacy impact analysis on an ongoing basis.
Conclusion
For many companies, especially SMBs, it will be a question of changing the way they think about data protection, and immediately increasing their level of cybersecurity.
This is because it has become more important than ever to put data privacy, and in particular data associated with personal information, into practice.
Here are some of the best practices to implement in a Zero Trust mindset.
- Perform a security audit of your environment because you can only defend what you know.
- Classify data and assets based on their privacy requirements.
- Secure sensitive data with encryption.
- Implement two-factor authentication (MFA).
- Adequately protect your servers and endpoints using a MDR (Managed Detection and Response) solution.
- Train employees on privacy, data security and phishing.
- Implement a managed security information and event management solution to minimize your reaction times and maintain the mandatory log of all breaches.
Doing this is a two for one! Not only are you adapting to the current threat landscape, but you are also preparing for PL 64 at the same time.
How many of these 7 basic elements have you checked off the list?
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)

