Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 Like most businesses, in order to operate, you need to store sensitive personal information such as names, social insurance numbers, credit card numbers and other sensitive data needed to identify your customers, your employees or partners.
Like most businesses, in order to operate, you need to store sensitive personal information such as names, social insurance numbers, credit card numbers and other sensitive data needed to identify your customers, your employees or partners.
The context of Law 25
There is no shortage of examples of companies that have stored sensitive, personal information without adequately protecting it. Just think of the case of Desjardins, whose 4.2 million customers were affected by data theft.
The images below illustrates on the one hand the gravity of data losses associated with internal theft, and on the other hand the fact that the exfiltration of data corresponds to 68% of the attacks.
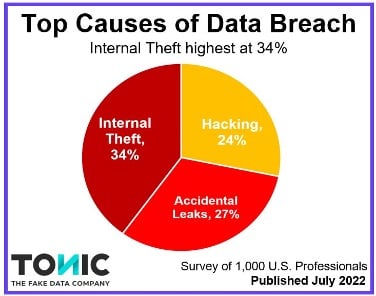
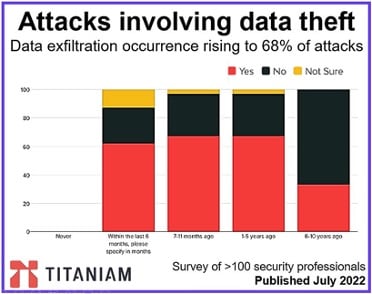
It is this situation that led the Quebec legislation to adopt Law 25 (aka Bill 64), in order to force companies, using extremely dissuasive penalties, to better protect the personal information of citizens.
It is important to remember that the fines could reach 25 million dollars, or 4% of the global sales of the previous financial year, whichever amount is higher. These amounts are doubled in the case of a repeat offence.

The consequences of a breach on your business
Obviously, data breaches, and particularly those involving personal information, can have very serious repercussions on the individuals who are victims, but also on the company, if they are not detected or (better still ) blocked in a timely manner.
Therefore, the implementation of appropriate technological tools is of the utmost importance to detect them.
In this article, we will therefore examine how Microsoft can help you comply with the requirements of Law 25 in order to minimize the risk of sanctions by better protecting the data entrusted to you.
What are the main obligations of Law 25?
The gradual enforcement of Law 25 concerning the protection of personal information could lead you to believe that you have time before you need to comply with the new requirements.
But time is ticking.
New corporate responsibilities and obligations
Even if the administrative sanctions and monetary penalties will only apply starting in September 2023, the obligation to appoint a person in charge of the protection of personal information as well as that of declaring confidentiality incidents to the Commission d'accès à l'information (CAI) takes effect starting September 22, 2022.
In the event of a privacy incident involving personal information, the law requires companies to:
- Take reasonable measures to reduce the risk of harm being caused to the persons concerned and thus prevent new incidents of the same nature from occurring;
- Notify the Commission and the person concerned if the incident presents a risk of serious injury;
- Keep a register of incidents, a copy of which must be sent to the Commission at its request;
You still need to be able to detect these incidents!
Companies have until September 22, 2022 to appoint a privacy officer and implement their privacy incident response plan.
What is a Privacy Incident?
A privacy or confidentiality incident occurs when there is unauthorized access by law to personal information, its use or its communication, as well as its loss or any other form of attack on its protection.
Here are some examples of privacy incidents:
- A member of your staff who consults personal information not necessary for the exercise of his functions by overriding the access rights which have been granted to him, or a hacker who infiltrates a system.
- A member of your staff who uses personal information from a database to which he has access as part of his duties for the purpose of impersonating a person.
- A communication made in error to the wrong person by his employer.
- A person who loses or has stolen documents containing personal information.
- A person who interferes with a database containing personal information in order to alter it.
Because the law aims to improve data governance and privacy practices, it necessarily implies a significant technological aspect to be able to monitor and respond to privacy incidents.
For personal information to remain private, it must be secure.
This means that you must have a solid data management policy associated with adequate data protection.
Which Microsoft technologies detect privacy incidents?
We can agree that the ever-increasing amount of personal data collected by companies raises the question of the confidentiality of personal information and therefore that of regulatory compliance with Law 25.
It is also safe to say that with the industrial fabric of Quebec being made up mainly of SMBs, Microsoft 365 Business Premium should be the norm.
How can M365 Business Premium's information protection tools help SMBs meet the challenge of locating, classifying and protecting data?
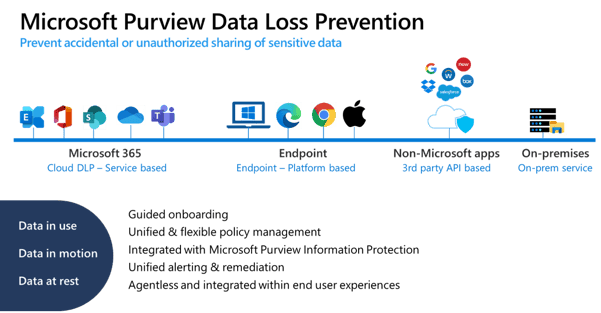
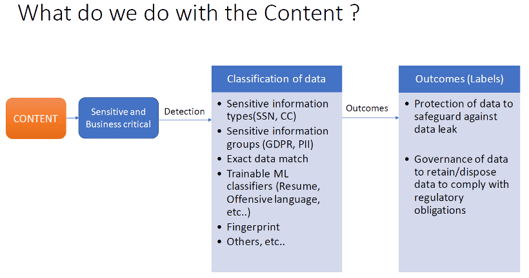
The image below illustrates Microsoft's approach.
Some features require Microsoft 365 E5. However, the Microsoft Purview Information Protection and Microsoft Purview Data loss prevention (DLP) technologies explained below are an integral part of Microsoft Business Premium.
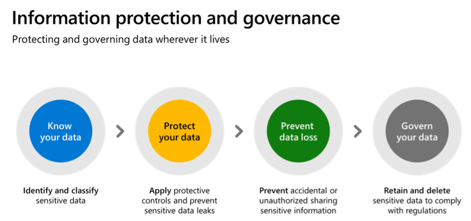
The initial questions you should ask yourself are:
1. Do you know where your critical and sensitive data is and how it is being used?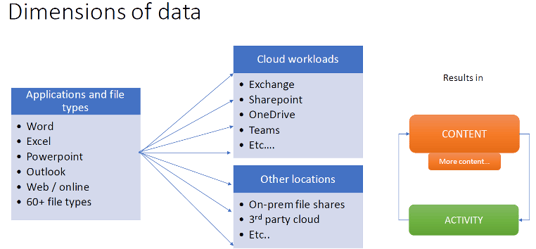
Microsoft Purview Information Protection
Microsoft Purview Information Protection helps discover, classify, protect, and manage sensitive information in documents and emails by applying labels. This allows you to control who has access to company information, by applying restrictions on transfer, copying or printing.
Microsoft Purview Data loss prevention (DLP)
With Microsoft Purview Data loss prevention (DLP) for Exchange Online, SharePoint Online, and OneDrive for Business, businesses can automatically identify, monitor, and protect sensitive information in emails and files (including files stored in Microsoft Teams file repositories ). This helps prevent employees from sharing sensitive information such as credit card information and social insurance numbers.
Conclusion
You can implement cybersecurity practices without privacy protection, but you cannot implement privacy practices without cybersecurity.
And even if your data collection policies comply with the law, if you don't protect that data with adequate security measures, such as multi-factor authentication, advanced endpoint security and access management, you have a high risk of a data breach. And who would want to attract the attention of regulators like that?
Since you are using Microsoft M365 Business Premium or Microsoft E3, you already have Microsoft Purview Information Protection and Microsoft Purview Data loss prevention (DLP). You just need to configure them.
If you haven't started your Law 25 compliance process, you should get started right away and not wait to upgrade your security level.
You will thus be able to prove that you have put in place the appropriate measures to protect the personal information in your custody and that you have effective incident management.
Present's cybersecurity experts are at your disposal so that you can focus on the success of your business with peace of mind, while minimizing your risk of breaches.
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)