Present Blog – IT Thought Leadership
Blog Present-IT thought leadership
Blog Present-IT thought leadership
IT thought leadership blog for CIOs and CTOs in Canada seeking resources to drive IT as a business contributor: hybrid cloud, infrastructure, managed services and security and IT recruitment.
 As a Managed Security Services Provider, we come into contact with SMB executives who are sometimes perplexed or helpless regarding the security attacks that hit the headlines, day after day, at an accelerating pace.
As a Managed Security Services Provider, we come into contact with SMB executives who are sometimes perplexed or helpless regarding the security attacks that hit the headlines, day after day, at an accelerating pace.
Here are, however, the top 5 myths they're still exposed to concerning their IT security.
Myth 1: My company is too small to be targeted by hackers
Hackers see SMEs as easy prey. They are the victims of the majority of attacks (64%) precisely because they are poorly protected.
They also remain vulnerable to threats such as disgruntled employees, competition, social engineering, and compromised email.
Myth 2: I already have a firewall, antivirus, and backup solution. Do I really need more?
This set of solutions was certainly sufficient in the past. But today, the majority of cyber-attacks are sophisticated enough to bypass basic business security precautions. What worked yesterday is no longer sufficient to protect against today's threats. Security must imperatively be adapted.
And of course, it is much more economical to fix this problem before it happens, especially knowing that the average breach costs an SME around $ 200,000, and that sum is increasing.
Myth 3: Why would a criminal want my data? They are not that precious!
In fact, your data is often more valuable than you might think, when sold underground. Would your main competitor pay $ 10,000 for your business plans, acquisition plans, or marketing strategy? Would someone pay for your usernames and passwords, so they can connect to your network without your knowledge? Very probably.
Moreover, in the case of ransomware, the criminal knows that you need your data to function and that you will pay to obtain the decryption key.
Myth 4: I'm already covered with my managed services contract.
When you signed up for your managed services contract, your provider probably included the best tools to manage your network, and provide basic security.
The problem is cybercriminals have improved their skills and are now attacking in ways that are not covered by the tools in place. And while you still need the coverage you have today, you need to consider other coverage that is absolutely necessary today to adequately protect yourself.
Myth 5: I am covered by my cyber insurance.
The goal of cyber insurance is to transfer some of the risk associated with a security breach to the insurer.
But the reality is that purchasing this insurance does not exempt the customer from having adequate security.
Indeed, although cyber insurance can be useful, it is not a substitute for the establishment and maintenance of appropriate security and training policies.
Insurance companies will not pay if companies cannot prove that they have implemented the necessary means to protect their environments against cybersecurity threats. It is important to distinguish between what is preventable and what is beyond the control of the company.
Now how should you manage the risk?
We offer a simple process for decision makers.
Start from an indisputable observation

Threat + Vulnerabilities = Risk (the potential for loss or damage when a threat exploits a vulnerability)
Consider the scale of the threat
Recent surveys show that more than 80% of SMEs fear they are victims of a cyberattack, and rightly so.
According to Cybersecurity Ventures in 2021:
- Almost half of all cyber attacks are committed against SMBs.
- Every 11 seconds, a company will be victim of ransomware.
- Ransomware cyber attacks will cost businesses more than $ 20 billion.
Identify and start remedying your most glaring vulnerabilities
To find out where your business is at, take a look at our checklist.
15 essentials to protect your business against Cyberattacks.
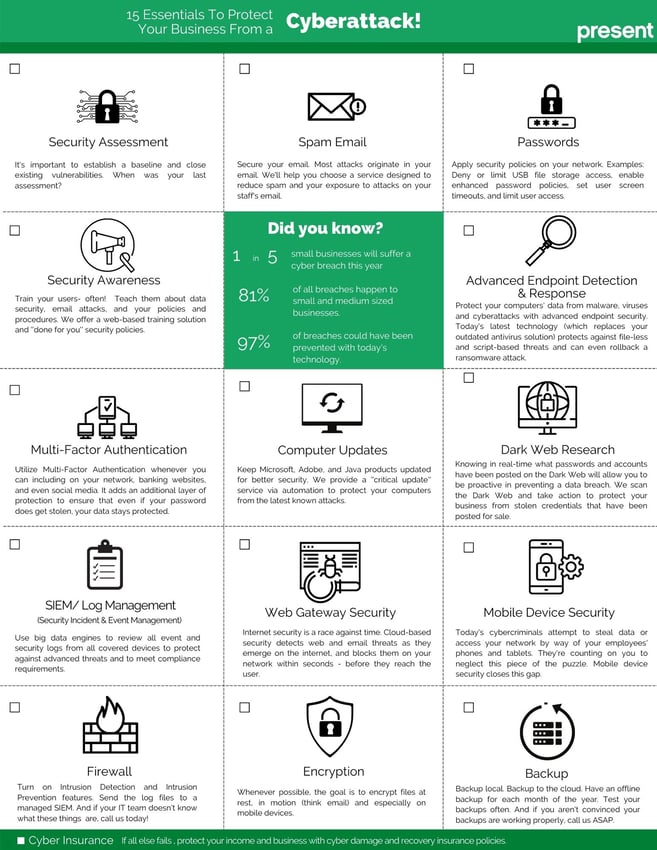
This list should help you identify cybersecurity blind spots in your organization and enable you to take the necessary steps to secure your business.
Still not sure where to start?
An important first step is to perform a security assessment. It will identify areas for improvement and develop a roadmap with recommendations tailored to your environment.
Cybercriminals take advantage of your outdated defense and capitalize on vulnerabilities in your systems.
- Where are your vulnerabilities?
- How severe are your risks?
- What should you do in order of priority?
- What would be the impact of the status quo on your company?
Still not sure? Contact us to have a discussion with one of our security experts
About Blog
The right use of technology addresses business challenges and drives business growth in all areas of an enterprise. We hope this blog will offer insight into developing strategies and tactics to enable you to identify those key drivers of growth and keep pace with and anticipate the rapid technology change of today.
Posts by Topic
- IT infrastructure (116)
- IT security (93)
- IT Innovation (59)
- Trends (51)
- Cloud (47)
- Managed services (47)
- Mobility (38)
- Digital transformation (29)
- CIO/IT leaders (28)
- Events (28)
- News (23)
- Microsoft 365 (17)
- Security (17)
- IBM (16)
- Disaster recovery (DR) (14)
- High availability (12)
- Recruitment (12)
- Storage (12)
- Big Data (11)
- Collaboration (11)
- AI (10)
- Case study (9)
- Office 365 (9)
- BYOD (8)
- Customer Experience (8)
- Hybrid Cloud (7)
- Current events (6)
- SAP Hana (5)
- Business intelligence (BI) (4)
- Converged infrastructure (4)
- Convergence / Hyper-convergence (4)
- Virtualization (4)
- Copilot (3)
- Future of retail (2)
- Retail (2)
- trend (2)
- Backups (1)
- Beacon (1)
- Blog Migrations (1)
- Contests (1)
- Infrastructure TI (1)
- Innovation TI (1)
- IoT (1)
- MDM (1)
- Stockage (1)
- Virtualisation (1)
- blockchain (1)
- cio (1)
- replication (1)
- Étude de cas (1)


